
Pivoting
Pivoting is when we use one compromised machine to exploit other hosts or networks
Pivoting Examples
An example would be a client-side “drive-by browser” attack
Once the attacker owns this machine inside the firewall, they can launch all further attacks from this compromised machine
When we pivot, we're taking advantage of the security and trust relationships between systems in an organization
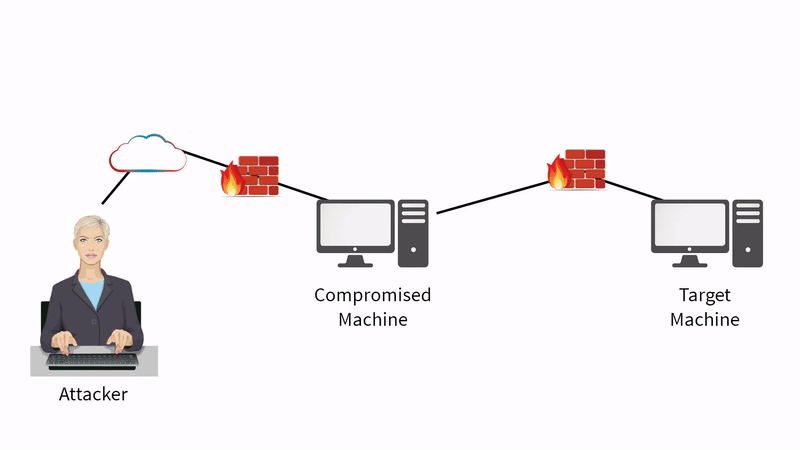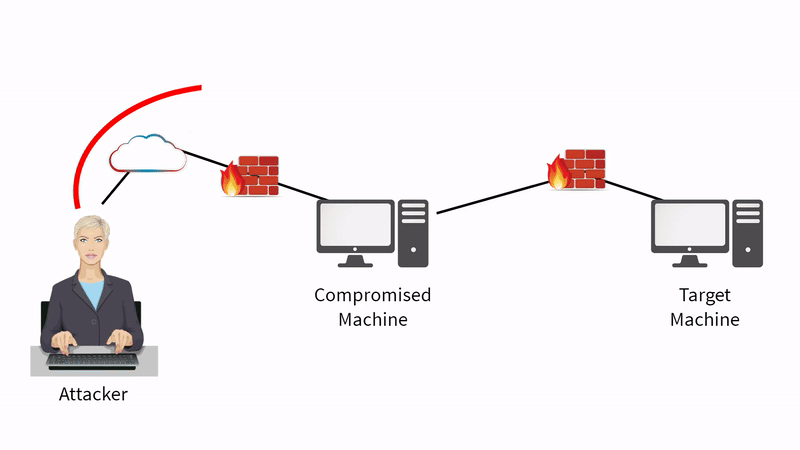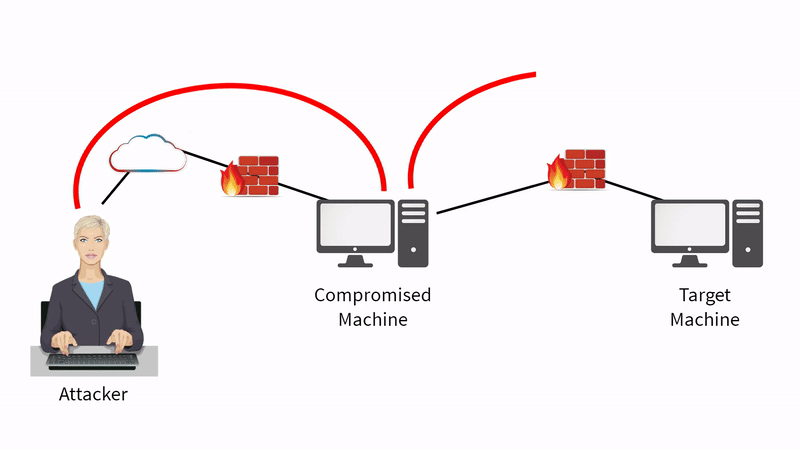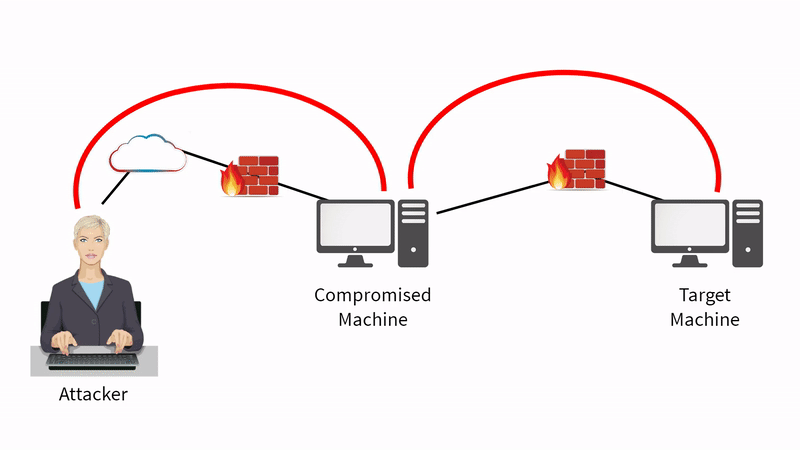
Let's say that, as an attacker, I've compromised the machine between the two firewalls above
In this case, I'd have complete control of the compromised machine through Meterpreter
I want to take advantage of that compromised machine and the trust that it is allowing to other systems in the organization
Any future exploits as an attacker can be almost funnelled through the compromised machine
We can launch an exploit from the compromised machine to the target machine on the right-hand side of the diagram
We may not be able to launch it directly from the attacker to the target machine because of the firewall rules that are in place, but we may be able to communicate from the compromised machine to the target machine
This is very common in organizations where a single workstation is compromised
The attacker will pivot from that initial machine to get access to more useful resources on the network, such as software repositories, employee databases, or credit card data
They'll funnel it through that compromised workstation and gain access to whatever resources that workstation can get to
It's like using the compromised system as a proxy for further attacks
Pivoting
Pivoting is when we use one compromised machine to exploit other hosts or networks
Pivoting Examples
An example would be a client-side “drive-by browser” attack
Once the attacker owns this machine inside the firewall, they can launch all further attacks from this compromised machine
When we pivot, we're taking advantage of the security and trust relationships between systems in an organization

Let's say that, as an attacker, I've compromised the machine between the two firewalls above
In this case, I'd have complete control of the compromised machine through Meterpreter
I want to take advantage of that compromised machine and the trust that it is allowing to other systems in the organization
Any future exploits as an attacker can be almost funnelled through the compromised machine
We can launch an exploit from the compromised machine to the target machine on the right-hand side of the diagram
We may not be able to launch it directly from the attacker to the target machine because of the firewall rules that are in place, but we may be able to communicate from the compromised machine to the target machine
This is very common in organizations where a single workstation is compromised
The attacker will pivot from that initial machine to get access to more useful resources on the network, such as software repositories, employee databases, or credit card data
They'll funnel it through that compromised workstation and gain access to whatever resources that workstation can get to
It's like using the compromised system as a proxy for further attacks
 Knowt
Knowt