
Network Attacks
Network Attack Methodology
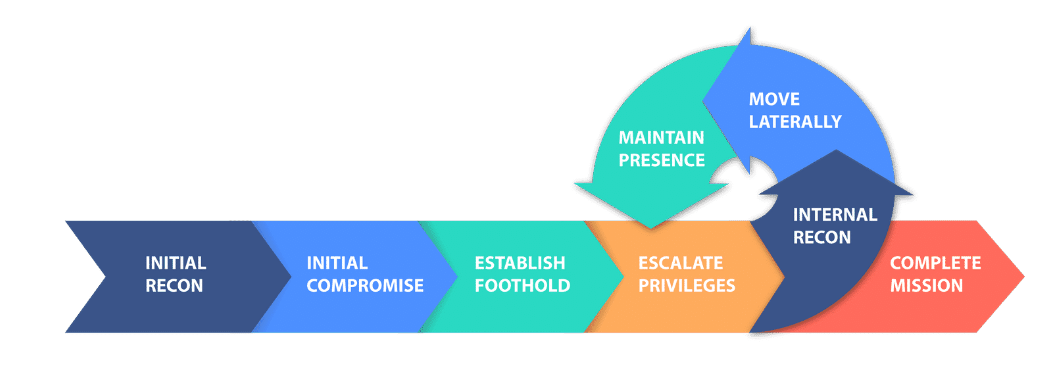
1. Reconnaissance
The information-gathering stage where you collect data about the target
A good reconnaissance phase is going to have a notebook full of data about the target
Examples:
Network Topology Information - This can be discovered through experimentation or probing the network.
Sometimes sloppy network administration means network diagrams are left for the taking on public shares.
Domain Names - What are the domain names that the target has registered?
Account Logins - What is the format of the account login that the target uses? Is it first initial, or last name? Is it first name dot last name? etc.
Most of the time, account names can be inferred by email addresses.
Operating Systems & Software - What kinds of operating systems and software are being used within the organization? etc.
One way to glean this information would be to review the job postings that the organization has posted on LinkedIn or job posting websites. Are they looking for certain expertise and operating systems or security platforms? You could make a safe assumption that those are the platforms being used in the organization.
Security Policies - What kinds of security policies are being used within the organization? What are the password complexity requirements? Do they have password lockout procedures? How do they reset passwords? Is there any way that a user can call up and have their password reset that could be useful information later on in the attack? etc.
Physical Security Systems – What kind of physical security systems do they have in place? etc.
Sometimes, a rational attacker’s goal could be quickly and efficiently realized simply by walking through the front door.
Employee Hangouts - You could do some shoulder surfing at the bar that everyone goes to after work, observe what kind of laptops or mobile devices they are using or get a look at how their ID badges are laid out and designed. etc.
Low-tech recon, such as
Dumpster Diving - People still throw away documents with account numbers and useful information can be gleaned from going through a person's garbage. Dumpster diving can be a useful form of reconnaissance
Physical Break-In - Sometimes the quickest way from point A to point B is to break in.
Social Engineering - A good attacker can take advantage of a person's emotions and con them into revealing important information about a target.
This can take place over the phone, via email, or even face-to-face.
2. Scanning
3. Vulnerability Identification
4. Exploitation of Those Vulnerabilities
Exploitation uses payloads to exploit a system
There are many different types of payloads
5. Post Exploitation
Maintaining Persistence
The idea is that once we have full control of a system, we want to maintain access, meaning that we want something in place where we don’t have to go through the exploitation phase again
Exploits don’t always work a second time and they’re not always 100% reliable
Real attackers attempt to be on the compromised system for a long time
They use the compromised system to attack other systems
Removing Forensic Evidence
Exfiltration
Network Attack Tools and Resources
Reconnaissance and Scanning
Vulnerability Identification and Exploitation
Vulnerability Scanning
Post Exploitation
Maintaining Persistence
Data Exfiltration
Network Attacks
Network Attack Methodology

1. Reconnaissance
The information-gathering stage where you collect data about the target
A good reconnaissance phase is going to have a notebook full of data about the target
Examples:
Network Topology Information - This can be discovered through experimentation or probing the network.
Sometimes sloppy network administration means network diagrams are left for the taking on public shares.
Domain Names - What are the domain names that the target has registered?
Account Logins - What is the format of the account login that the target uses? Is it first initial, or last name? Is it first name dot last name? etc.
Most of the time, account names can be inferred by email addresses.
Operating Systems & Software - What kinds of operating systems and software are being used within the organization? etc.
One way to glean this information would be to review the job postings that the organization has posted on LinkedIn or job posting websites. Are they looking for certain expertise and operating systems or security platforms? You could make a safe assumption that those are the platforms being used in the organization.
Security Policies - What kinds of security policies are being used within the organization? What are the password complexity requirements? Do they have password lockout procedures? How do they reset passwords? Is there any way that a user can call up and have their password reset that could be useful information later on in the attack? etc.
Physical Security Systems – What kind of physical security systems do they have in place? etc.
Sometimes, a rational attacker’s goal could be quickly and efficiently realized simply by walking through the front door.
Employee Hangouts - You could do some shoulder surfing at the bar that everyone goes to after work, observe what kind of laptops or mobile devices they are using or get a look at how their ID badges are laid out and designed. etc.
Low-tech recon, such as
Dumpster Diving - People still throw away documents with account numbers and useful information can be gleaned from going through a person's garbage. Dumpster diving can be a useful form of reconnaissance
Physical Break-In - Sometimes the quickest way from point A to point B is to break in.
Social Engineering - A good attacker can take advantage of a person's emotions and con them into revealing important information about a target.
This can take place over the phone, via email, or even face-to-face.
2. Scanning
3. Vulnerability Identification
4. Exploitation of Those Vulnerabilities
Exploitation uses payloads to exploit a system
There are many different types of payloads
5. Post Exploitation
Maintaining Persistence
The idea is that once we have full control of a system, we want to maintain access, meaning that we want something in place where we don’t have to go through the exploitation phase again
Exploits don’t always work a second time and they’re not always 100% reliable
Real attackers attempt to be on the compromised system for a long time
They use the compromised system to attack other systems
 Knowt
Knowt