
Lesson 1: Comparing Security Roles and Security Controls
Information Security (Infosec)
The protection of data resources from unauthorized access, attack, theft or damage
Data may be vulnerable because of the way it’s stored, transferred or processed
Therefore, the systems used to store, transmit and process data must demonstrate the properties of security, also known as the CIA Triad
CIA (AIC) Triad
Confidentiality
Having specific information that only certain people know
(Ensures that there’s no unauthorized disclosure of data)
Integrity
The data is stored and transferred as intended and any modification is authorized
(Ensures that there’s no unauthorized modification of data)
Availability
The information is accessible to those authorized to view or modify it
(Ensures that there’s no unauthorized withholding of data)
Security Properties
Non-Repudiation
A subject cannot deny doing something, such as creating, modifying, or sending a resource
Cybersecurity Framework (CSF)
A CSF (Cybersecurity Framework) is a list of activities and objectives undertaken to mitigate risks
CSFs allows an organization to
make an objective statement of its current cybersecurity capabilities, identify a target level of capability, and prioritize investments to achieve that target
create a structure for internal risk management procedures
provide an externally verifiable statement of regulatory compliance
save itself from building its security system on a foundation that fails to account for important security concepts and frameworks that correspond to its surroundings
There exist many different frameworks, each of which categorizes cybersecurity activities and controls in slightly different ways
These frameworks are non-regulatory in the sense that they don’t attempt to address the specific regulations of a specific industry but represent “best practice in IT security governance generally
Most frameworks are developed for an international audience, while some are focused on a domestic national audience
Most frameworks are associated with certification programs to show that staff and consultants can apply the methodologies successfully
NIST’s Cybersecurity Framework
NIST’s Five Cybersecurity Framework's Functions
Cybersecurity tasks, as well as information security tasks, can be classified as five functions following the framework developed by the NIST (National Institute of Standard and Technology) (Source: NIST)
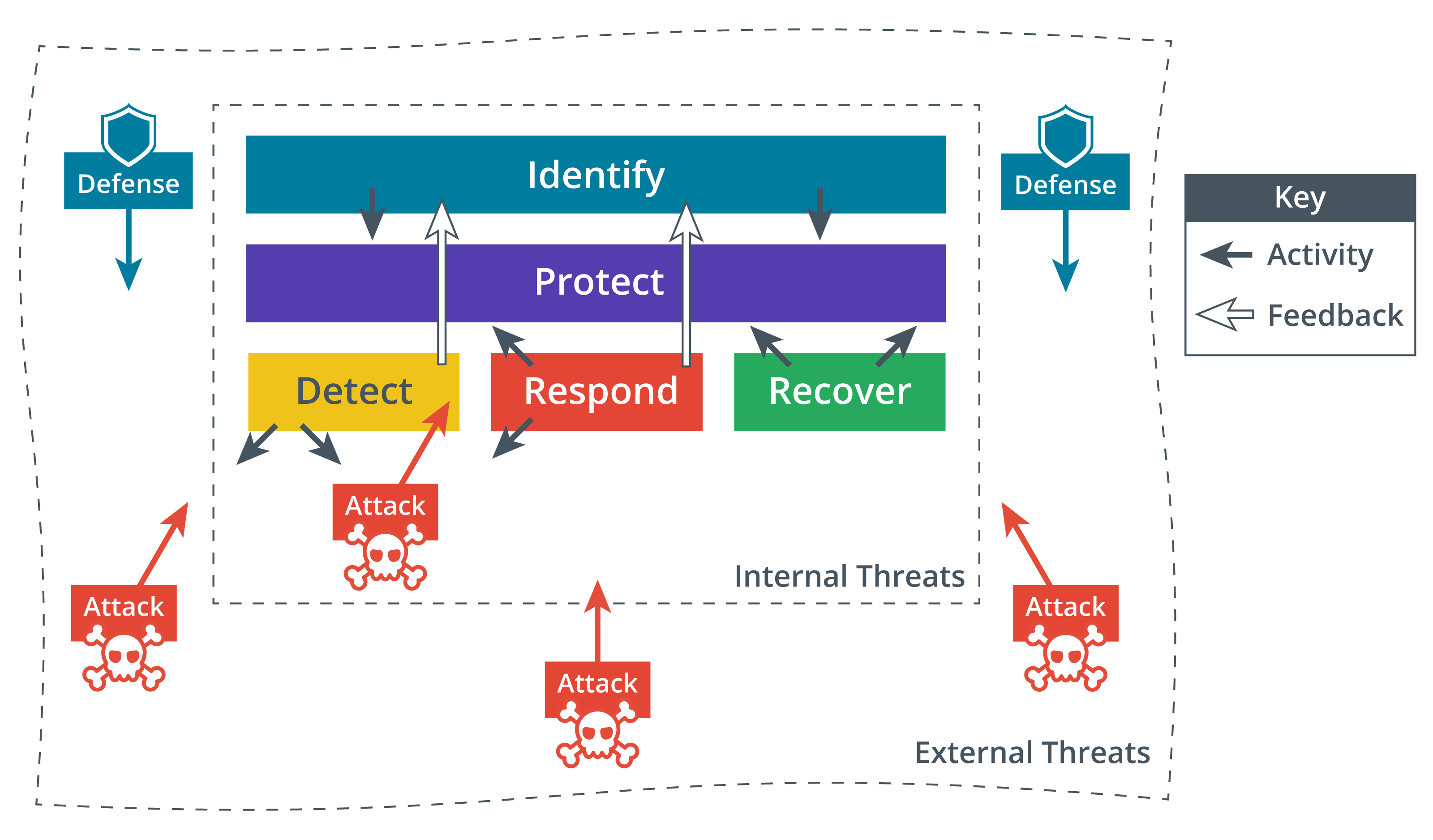
Identify
This function aims to develop an organizational understanding of managing cybersecurity risk to systems, people, assets, data and capabilities, as well as understanding the business context, the resources that support critical functions, and the related cybersecurity risks
This enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs
In short:
Develop security policies and capabilities
Evaluate risks, threats, and vulnerabilities
Recomment security controls to mitigate them
Protect
This function specifies appropriate safeguards to ensure the delivery of critical infrastructure services
This function supports the ability to limit or contain the impact of a potential cybersecurity event
In short:
Procure/develop, install, operate, and decommission IT hardware and software assets with security as an embedded requirement of every stage of this operations life cycle
Detect
This function defines the appropriate activities to identify the occurrence of a cybersecurity event
This function enables timely discovery of cybersecurity events
In short:
Perform outgoing and proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats
Respond
This function includes appropriate activities to take action regarding a detected cybersecurity incident
This function supports the ability to contain the impact of a potential cybersecurity incident
In short:
Identify, analyze, contain and eradicate threats to systems and data security
Recover
This function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident
This function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident
In short:
Implement cybersecurity resilience to restore systems and data if other controls are unable to prevent attacks
Common Information Security Competencies
Participate in risk assessments and testing of security systems and make recommendations
Specify, source, install, and configure secure devices and software
Set up and maintain document access control and user privilege profiles
Monitor audit logs, review user privileges, and document access controls
Manage security-related incident response and reporting
Create and test business continuity and disaster recovery plans and procedures
Participate in security training and education programs
Security Policy
A formalized statement that defines how security will be implemented within an organization
It describes the means the organization will take to protect the confidentiality, availability, and integrity of sensitive data and resources
Information Security Roles and Responsibilities
Security Roles and Responsibilities
Internal responsibility for security might be allocated to a dedicated department run by a Director of Security, CSO (Chief Security Officer) or CISO (Chief Information Security Officer)
Managers may have responsibility for a domain, such as building control, ICT (Information and Communications Technology), or accounting
Technical specialist staff have the responsibility for implementing, maintaining and monitoring the policy
Security might be made a core competency of systems and network administrators, which would go under the job title of an ISSO (Information Systems Security Officer)
Non-technical staff have the responsibility of complying with policy and with any relevant legislation
External responsibility for security lies mainly with directors or owners
NIST's National Initiative for Cybersecurity Education (NICE) categorizes job tasks and job roles within the cybersecurity industry (nist.gov/itl/applied-cybersecurity/nice/nice-framework-resource-center)
Information Security Bu
Business Units
Security Operations Center (SOC)
A SOC is a location where security professionals monitor and protect critical information assets across other business functions, such as finance, operations, sales/marketing, etc.
SOCs can be difficult to establish, maintain, and finance, which is why they’re usually employed by larger corporations, such as a government agency or a healthcare company
DevSecOps (Development, Security and Operations)
DevSecOps extends the boundary to security specialists and personnel, reflecting the principle that security is a primary consideration at every stage of software development and deployment, meaning that security considerations need to be made during requirements and planning phases, and not grafted at the end
Automates the integration of security at every phase of a software’s development lifecycle, from initial design through integration, testing, deployment, and software delivery (Source: IBM)
Cyber Incident Response Team (CIRT) / Computer Security Incident Response Team (CSIRT) / Computer Emergency Response Team (CERT)
A CIRT, CSIRT or CERT is seen as a single point of contact for the notification of security incidents
This function might be handled by the SOC or it might be established as an independent business unit
Security Control
Information security and cybersecurity assurance are met by implementing different security controls and cybersecurity frameworks that best suit the situation
Security control is something designed to give a system or data asset the properties of the CIA Triad
Security controls can also refer to a company’s cybersecurity frameworks, procedures, activities and technologies that are in place
Security Control Categories
Security controls can be divided into three broad categories that illustrates different ways of implementing security control
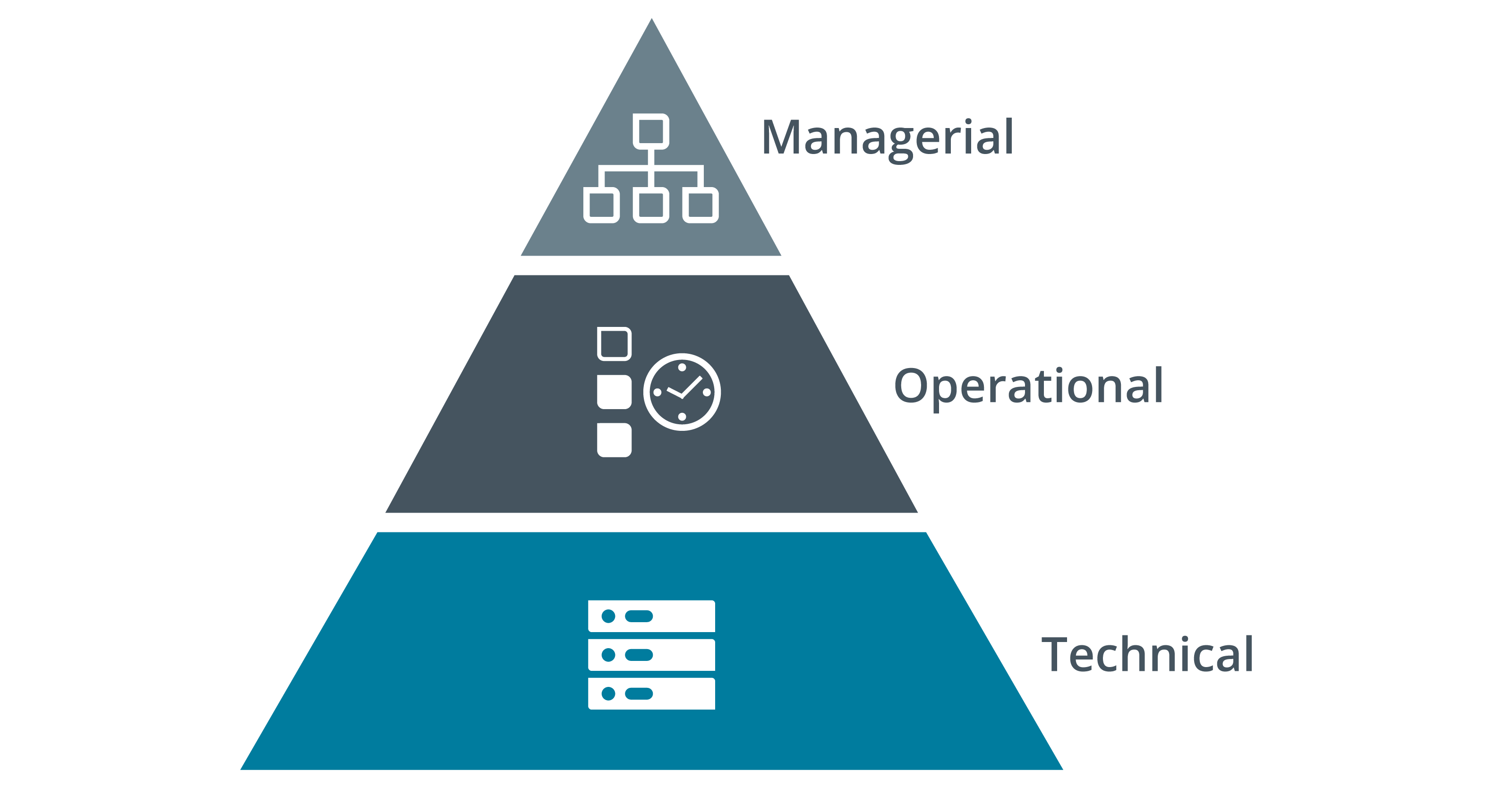
Technical/Logical Security Control
The security control is implemented either as a hardware, software or firmware system
Operational Security Control
The security control is implemented primarily by people rather than systems
Managerial Security Control
The security control gives oversight of the information system
Security Control Functional Types
Security controls can also be classified in types according to their goal or function
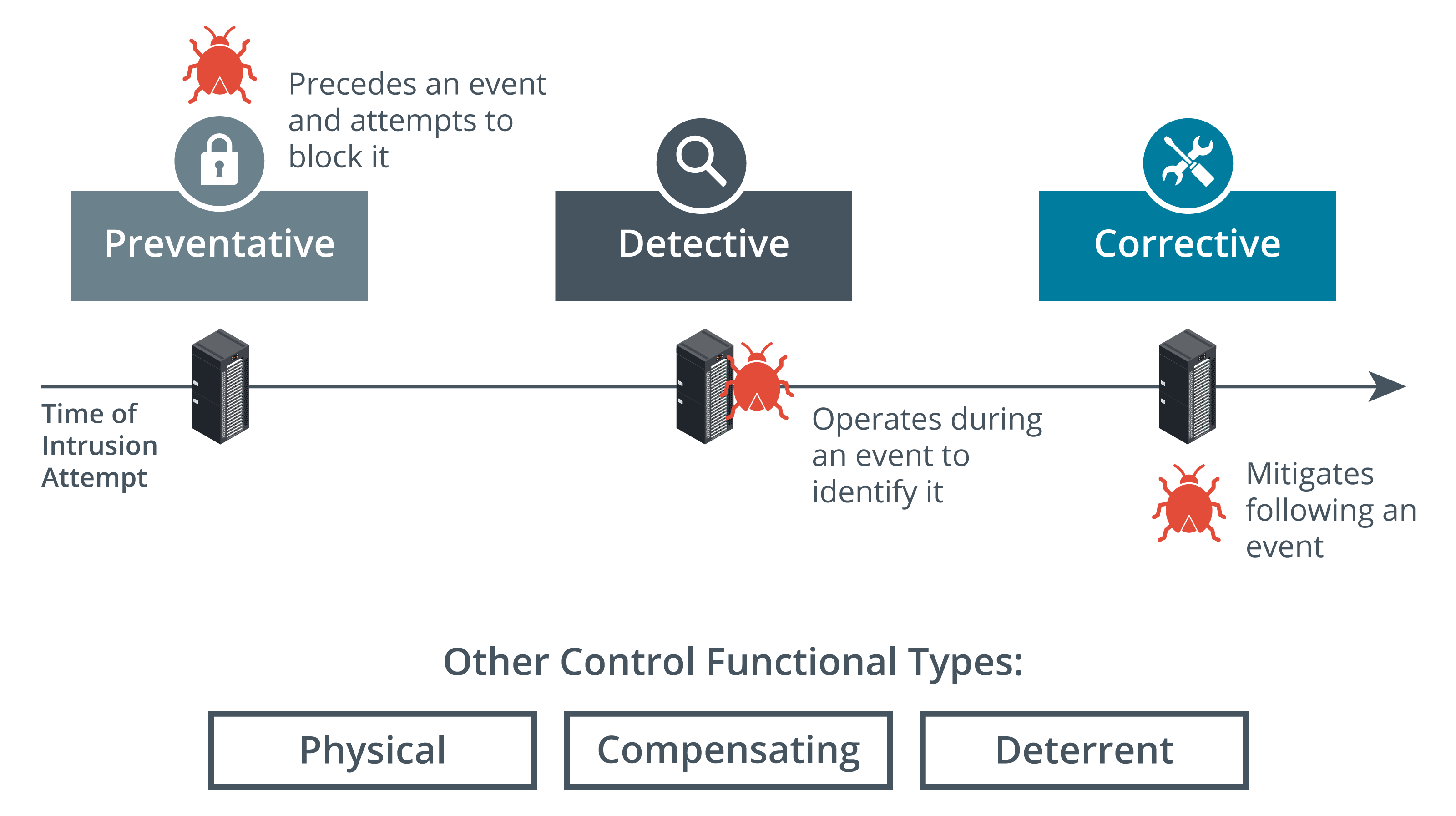
Preventive
The security control’s goal is to eliminate or reduce the likelihood that an attack can succeed
This security control operates before an attack can take place
Examples: ACLs, Firewalls, Filesystem objects, Anti-malware software, SOPs (Standard Operating Procedures), etc.
Detective
The security control’s function is to identify and record any attempted or successful intrusion
This security control operates during the progress of an attack
Example: Activity logs
Corrective
The security control’s function is to reduce the impact of an intrusion even
This security control is used after an attack
Examples: A backup system, a patch management system, etc.
Physical
This security control’s function is to deter and detect access to premises and hardware
Examples: Security cameras, locks, security guards, etc.
Deterrent
This security control’s goal is to psychologically discourage an attacker from attempting an intrusion
Example: Warning signs
Compensating
This security control’s function is to serve as a substitute for a principal control while offering the same or better level of protection through a different methodology or technology
Lesson 1: Comparing Security Roles and Security Controls
Information Security (Infosec)
The protection of data resources from unauthorized access, attack, theft or damage
Data may be vulnerable because of the way it’s stored, transferred or processed
Therefore, the systems used to store, transmit and process data must demonstrate the properties of security, also known as the CIA Triad
CIA (AIC) Triad
Confidentiality
Having specific information that only certain people know
(Ensures that there’s no unauthorized disclosure of data)
Integrity
The data is stored and transferred as intended and any modification is authorized
(Ensures that there’s no unauthorized modification of data)
Availability
The information is accessible to those authorized to view or modify it
(Ensures that there’s no unauthorized withholding of data)
Security Properties
Non-Repudiation
A subject cannot deny doing something, such as creating, modifying, or sending a resource
Cybersecurity Framework (CSF)
A CSF (Cybersecurity Framework) is a list of activities and objectives undertaken to mitigate risks
CSFs allows an organization to
make an objective statement of its current cybersecurity capabilities, identify a target level of capability, and prioritize investments to achieve that target
create a structure for internal risk management procedures
provide an externally verifiable statement of regulatory compliance
save itself from building its security system on a foundation that fails to account for important security concepts and frameworks that correspond to its surroundings
There exist many different frameworks, each of which categorizes cybersecurity activities and controls in slightly different ways
These frameworks are non-regulatory in the sense that they don’t attempt to address the specific regulations of a specific industry but represent “best practice in IT security governance generally
Most frameworks are developed for an international audience, while some are focused on a domestic national audience
Most frameworks are associated with certification programs to show that staff and consultants can apply the methodologies successfully
NIST’s Cybersecurity Framework
NIST’s Five Cybersecurity Framework's Functions
Cybersecurity tasks, as well as information security tasks, can be classified as five functions following the framework developed by the NIST (National Institute of Standard and Technology) (Source: NIST)

Identify
This function aims to develop an organizational understanding of managing cybersecurity risk to systems, people, assets, data and capabilities, as well as understanding the business context, the resources that support critical functions, and the related cybersecurity risks
This enables an organization to focus and prioritize its efforts, consistent with its risk management strategy and business needs
In short:
Develop security policies and capabilities
Evaluate risks, threats, and vulnerabilities
Recomment security controls to mitigate them
Protect
This function specifies appropriate safeguards to ensure the delivery of critical infrastructure services
This function supports the ability to limit or contain the impact of a potential cybersecurity event
In short:
Procure/develop, install, operate, and decommission IT hardware and software assets with security as an embedded requirement of every stage of this operations life cycle
Detect
This function defines the appropriate activities to identify the occurrence of a cybersecurity event
This function enables timely discovery of cybersecurity events
In short:
Perform outgoing and proactive monitoring to ensure that controls are effective and capable of protecting against new types of threats
Respond
This function includes appropriate activities to take action regarding a detected cybersecurity incident
This function supports the ability to contain the impact of a potential cybersecurity incident
In short:
Identify, analyze, contain and eradicate threats to systems and data security
Recover
This function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident
This function supports timely recovery to normal operations to reduce the impact from a cybersecurity incident
In short:
Implement cybersecurity resilience to restore systems and data if other controls are unable to prevent attacks
Common Information Security Competencies
Participate in risk assessments and testing of security systems and make recommendations
Specify, source, install, and configure secure devices and software
Set up and maintain document access control and user privilege profiles
Monitor audit logs, review user privileges, and document access controls
Manage security-related incident response and reporting
Create and test business continuity and disaster recovery plans and procedures
Participate in security training and education programs
Security Policy
A formalized statement that defines how security will be implemented within an organization
It describes the means the organization will take to protect the confidentiality, availability, and integrity of sensitive data and resources
Information Security Roles and Responsibilities
Security Roles and Responsibilities
Internal responsibility for security might be allocated to a dedicated department run by a Director of Security, CSO (Chief Security Officer) or CISO (Chief Information Security Officer)
Managers may have responsibility for a domain, such as building control, ICT (Information and Communications Technology), or accounting
Technical specialist staff have the responsibility for implementing, maintaining and monitoring the policy
Security might be made a core competency of systems and network administrators, which would go under the job title of an ISSO (Information Systems Security Officer)
Non-technical staff have the responsibility of complying with policy and with any relevant legislation
External responsibility for security lies mainly with directors or owners
NIST's National Initiative for Cybersecurity Education (NICE) categorizes job tasks and job roles within the cybersecurity industry (nist.gov/itl/applied-cybersecurity/nice/nice-framework-resource-center)
Information Security Bu
Business Units
Security Operations Center (SOC)
A SOC is a location where security professionals monitor and protect critical information assets across other business functions, such as finance, operations, sales/marketing, etc.
SOCs can be difficult to establish, maintain, and finance, which is why they’re usually employed by larger corporations, such as a government agency or a healthcare company
DevSecOps (Development, Security and Operations)
DevSecOps extends the boundary to security specialists and personnel, reflecting the principle that security is a primary consideration at every stage of software development and deployment, meaning that security considerations need to be made during requirements and planning phases, and not grafted at the end
Automates the integration of security at every phase of a software’s development lifecycle, from initial design through integration, testing, deployment, and software delivery (Source: IBM)
Cyber Incident Response Team (CIRT) / Computer Security Incident Response Team (CSIRT) / Computer Emergency Response Team (CERT)
A CIRT, CSIRT or CERT is seen as a single point of contact for the notification of security incidents
This function might be handled by the SOC or it might be established as an independent business unit
Security Control
Information security and cybersecurity assurance are met by implementing different security controls and cybersecurity frameworks that best suit the situation
Security control is something designed to give a system or data asset the properties of the CIA Triad
Security controls can also refer to a company’s cybersecurity frameworks, procedures, activities and technologies that are in place
Security Control Categories
Security controls can be divided into three broad categories that illustrates different ways of implementing security control

Technical/Logical Security Control
The security control is implemented either as a hardware, software or firmware system
Operational Security Control
The security control is implemented primarily by people rather than systems
Managerial Security Control
The security control gives oversight of the information system
Security Control Functional Types
Security controls can also be classified in types according to their goal or function

Preventive
The security control’s goal is to eliminate or reduce the likelihood that an attack can succeed
This security control operates before an attack can take place
Examples: ACLs, Firewalls, Filesystem objects, Anti-malware software, SOPs (Standard Operating Procedures), etc.
Detective
The security control’s function is to identify and record any attempted or successful intrusion
This security control operates during the progress of an attack
Example: Activity logs
Corrective
The security control’s function is to reduce the impact of an intrusion even
This security control is used after an attack
Examples: A backup system, a patch management system, etc.
Physical
This security control’s function is to deter and detect access to premises and hardware
Examples: Security cameras, locks, security guards, etc.
Deterrent
This security control’s goal is to psychologically discourage an attacker from attempting an intrusion
Example: Warning signs
Compensating
This security control’s function is to serve as a substitute for a principal control while offering the same or better level of protection through a different methodology or technology
 Knowt
Knowt
